We recently acquired a new client that was previously a victim of a cyber crime, specifically ransomware. After the IR team finished, the files were recovered ( I am not privy to the details, but I’m guessing that the insurance paid the ransom) and systems restored. Their old IT company was fired, and the IR team did little to fix some of the underlying problems that arose from the incident.
Here are some of the issues i have run in to so far:
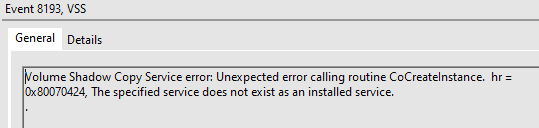
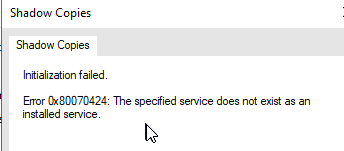
The volume shadow copy service does not work, rendering backups impossible.
DISM utility will not run in on-line mode, because it cannot find the source files.
SFC Scan finds files that are corrupted and states that they cannot be repaired.
Hackers being clever people, are going to modify your server to make sure that the tools that you can use to restore your files (backups, shadow copies, etc.) are either disabled or corrupted.
Note: Before following any of these steps and until you are able to fix the issue, make a backup of your data using Robocopy or another file level utility utility (does not require VSS). While not ideal and slow, it will offer some level of data protection in the meantime.
My first step was to restore the operating system files via DISM. While there are several ways that DISM image repair could be made inaccessible to Internet, including pointing to a non-existent WSUS server, my immediate concern was running a DISM image repair and the following steps allowed me to do that.
In order to do this, I downloaded an image file of the OS and mounted it.
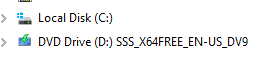
The mounted image appeared as drive letter D so I ran the following DISM command:
DISM /Online /Cleanup-Image /RestoreHealth /source:WIM:D:\Sources\Install.wim:1 /LimitAccess
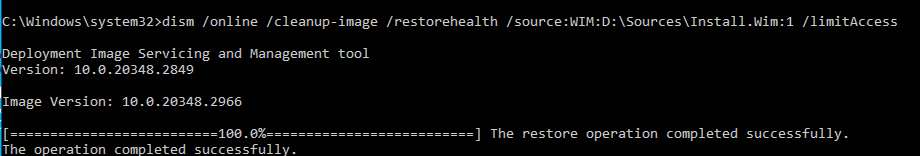
This step allowed me to run and complete a DISM image repair. Once DISM repair completed, I was able to run SFC Scan successfully.
The next thing to tackle was VSS.
Check that the VSS services are working properly. Make sure that VSS and SWPRV are present and set to manual startup.
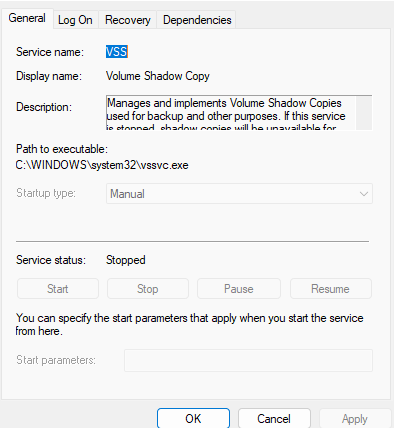
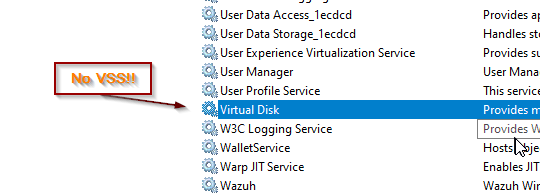
If they are not, run the following commands to re-register the VSS services.
regsvr32 ole32.dll
regsvr32 oleaut32.dll
regsvr32 vss_ps.dll
Vssvc /Register
regsvr32 /i swprv.dll
regsvr32 /i eventcls.dll
regsvr32 es.dll
regsvr32 stdprov.dll
regsvr32 vssui.dll
regsvr32 msxml.dll
regsvr32 msxml3.dll
regsvr32 msxml4.dllHere’s what you can check for when the VSS service is missing:
Are the registry’s VSS key entries missing?
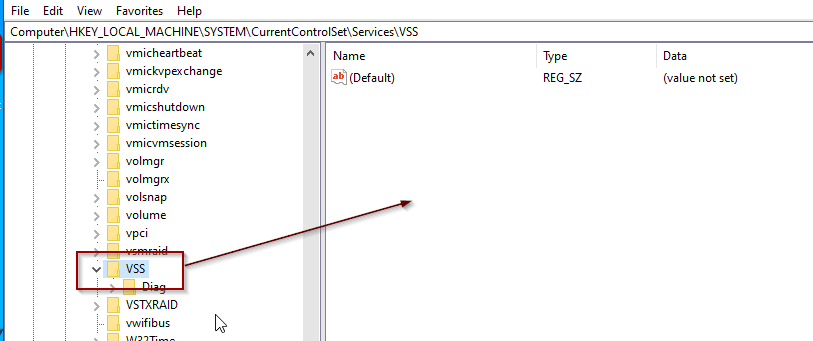
A healthy VSS registry should have the following keys and sub keys:
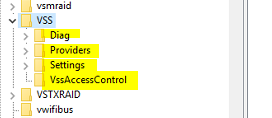
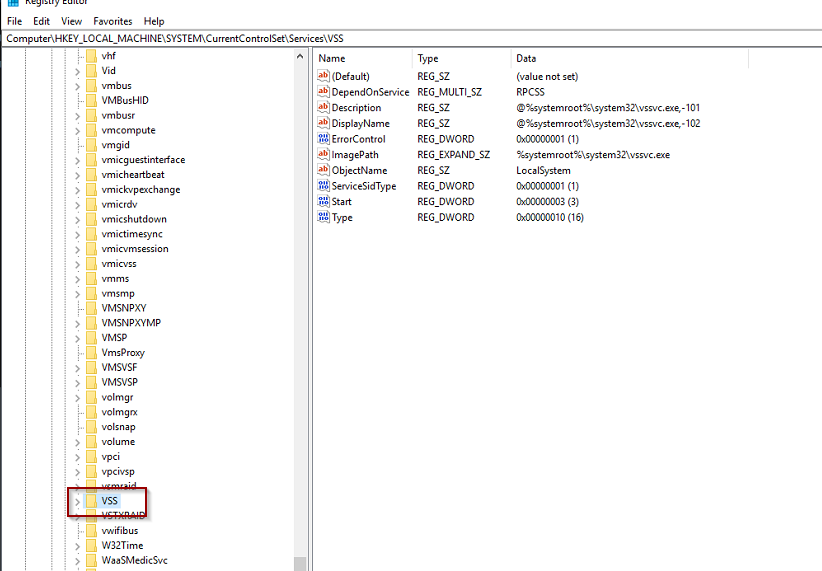
You can try to follow the steps in this article OR import the missing keys from a known good registry. keep in mind however that the recommended action after a ransomware attack is for the complete reformatting of the operating system.
Here are some helpful guides on how to repair VSS issues:
https://helpdesk.kaseya.com/hc/en-gb/articles/229020388-Microsoft-VSS-Troubleshooting
https://winaero.com/how-to-restore-the-missing-microsoft-software-shadow-copy-provider-service/
