When configuring your edge firewall, blocking outbound port 25 should be modus operandi. The reason for this is simple: no matter how much security you have, a piece of malware can still infect a computer in your LAN. If it happens to be a spamming malware, you may find your IP address blocked by several RBL’s within a few hours.
If you operate a small network and don’t have a separate subnet for your wireless guests, or if you don’t have network protection services to verify compliance, then outbound SMTP port blocking can be a lifesaver.
Blocking outbound SMTP traffic will not stop malware or user indiscretions, but it will stop spamming malware from using your Internet connection as a conduit for SPAM. This in turn, will save your company from a possible RBL listing (Real Time Block List). If you have an on-premise Exchange server, getting block listed is no fun. Your Exchange server will not be able to relay mail to domains that use RBL’s to trust other E-mail servers.
There are many types of routers, firewalls and edge devices. For our example, we will use a Sonicwall TZ-215 appliance with enhanced OS however, the process is similar for many other Sonicwall enhanced OS appliance models. The premise is simple: create a firewall rule that allows the local Exchange server to relay SMTP packets while preventing other hosts in your LAN from doing the same.
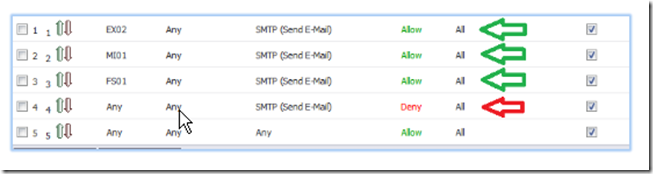
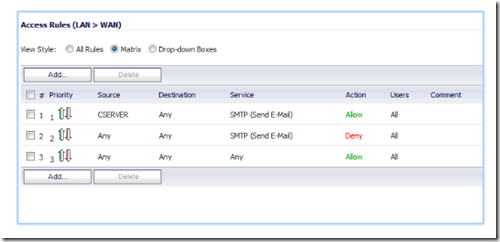
Let’s begin. In the example below, we have rules # 1-3 which specifically allows the Exchange server (EX02) and two other servers to relay. Rule # 4 blocks any other host from doing so.
You need to make sure that the allow rules precede the deny rules. The reason for this is because the firewall reads the rules in linear fashion starting from rule # 1. As soon as it finds a match, it looks no further. If we were to reverse rules # 1 and 4 in the example above, the firewall would look at rule # 1, see that ANY (all hosts) is prevented from relaying and drop the packet. It would look no further and thus not notice that further down there is a rule to allow EX02 to relay.
If on the other hand, we set up the rules exactly as shown above, the firewall would process rule # 1, see that EX01 is allowed to relay and allow the outbound packet to traverse. For this reason, your allow rules should be placed before your deny all rule.
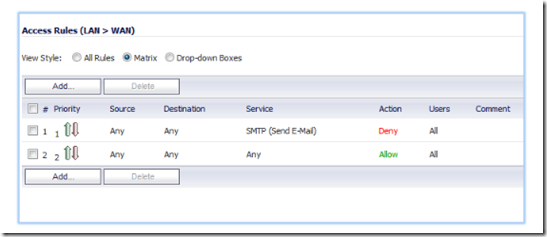
To create the firewall rules, open your Sonicwall management interface and navigate to firewall, then access rules. To prevent LAN users from sending outbound SMTP, select from LAN to WAN.
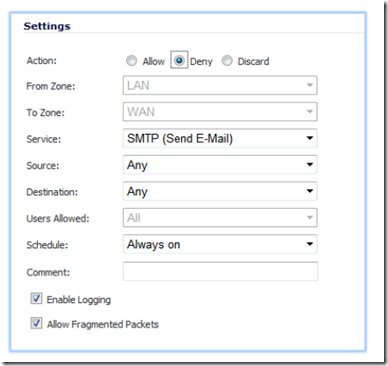
Click on the add button and copy the settings as shown below. In the action setting, select deny. Select SMTP as the service and Any as the source and destinations.
This will be our deny all rule, it will deny all SMTP port 25 traffic originating from the LAN subnet and destined for the WAN.
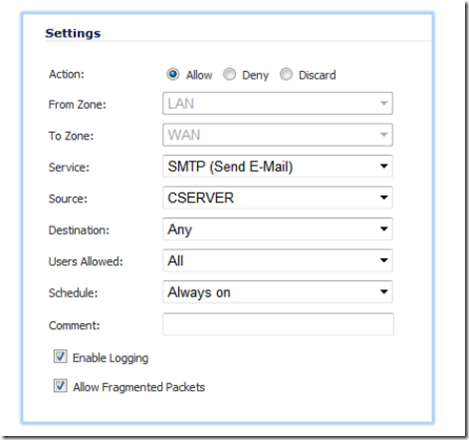
Now we need to create the allow list. This list will include all servers and devices which will be allowed to relay. Click on the add button to create a new rule. In the action settings, select allow. Select SMTP as the service, your SMTP server as the source and any as the destination.
Repeat the above step for all the hosts that need to relay.
Once you have finished, click on the priority arrows to move the rules up and down the priority list. The rules that allows your mail hosts to relay should be first followed by the ANY>ANY>Deny rule. The ANY > ANY allow rule should be the last on the list.
To test whether you configured the rules correctly, connect to an E-mail server and from a command prompt, type:
telnet mail.falconitservices.net 25
The result should be a 220 message. Now try the same command from another host and you should get a connection refused message.

cheriestoy@gmail.com