CVE-2021-34527 is a serious flaw that can grant total ownership of a domain to an attacker by giving him/her control of a domain controller by creating a new account of any group membership. This article will show you how to manually mitigate the problem. Manual mitigation is necessary if you have servers that are no longer supported and thus cannot be updated using the CVE-2021-34527 hotfix that is available from Microsoft.
The risk factor is high due to the attack complexity being low. It’s unknown if this vulnerability affects local accounts as of the time of this writing. Thankfully, the exploit is required to run by a users in the authenticated user’s group of the domain; otherwise the myriad of small networks that allow BYOD, IoT and other devices on the same segment would surely fall victim in no time at all. This leaves domain connected PC’s with poor security and/or insiders as the main attack vector.
Please note that applying the fixes below will not only affect print server but fax servers as well. If you share Windows fax and use it as a fax server, clients will no longer be able to connect to the centralized fax service and send faxes from their PC’s.
Enough said, let’s open this Oreo and get to the filling.
Single Server – Simple Network Server Mitigation
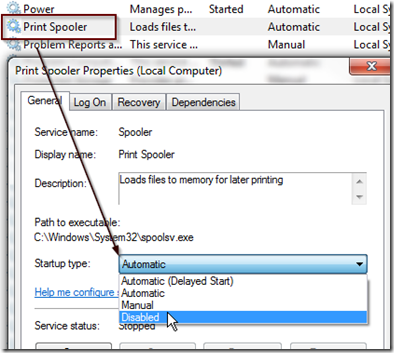
If you have a single server and it’s not used to remote print (i.e. print server) you can simply turn off the print spooler to mitigate the exploit. This will block remote spoolers and local print jobs. I don’t know why you would need to print from a server/DC, but if you don’t, follow best practices that states you should turn off any service you don’t need or use.
To do this, log on to the server and execute the following commands:
Stop-Service -Name Spooler –Force
Set-Service -Name Spooler -StartupType Disabled
You can also disable the service in the service manager console as shown below.
Multiple Server Mitigation
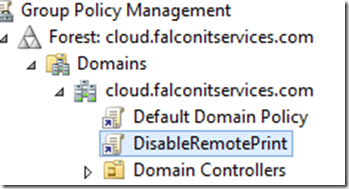
If you have multiple servers it may be too time consuming to disable the print spooler on each server. You can disable remote print using a GPO. This will prevent remote spooling and block the exploit while allowing you to send local print jobs directly to a printer. Open the group policy management console and create a policy named DisableRemotePrint.
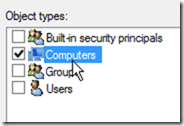
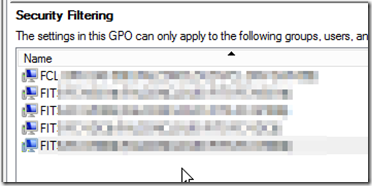
In the security filtering box, remove authenticated users group and add all your domain controllers, servers that are not print servers and any other device you want to stop from accepting remote print jobs. Make sure to check computers from the object types.
Add the servers or groups of servers that are not print servers to the policy. Make sure to add all DC’s as these are the most vulnerable.
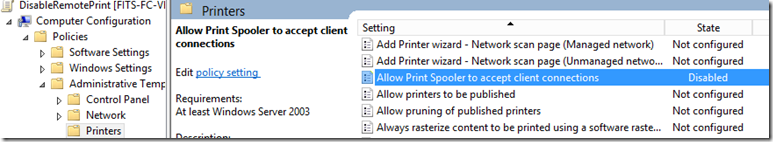
Right click on the GPO to edit and expand computer configuration –> administrative templates –> printers then disable ‘allow print spooler to accept client connections’.
This will disable remote print spooling (i.e. the server cannot act as a print server).
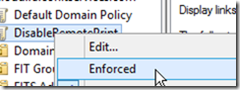
Don’t forget to enforce the policy!
Mitigating Print Servers
If you have a Windows print server on your network, you cannot disallow remote connections on the print spooler, otherwise it will stop functioning as a print server. Until Microsoft releases a hotfix for this issue, make sure that your print server is not a DC, it should be a member server only. I understand that some SMB’s cannot afford to have one server per role and a single server may have multiple roles on an SMB network; however DC’s should only be performing ADDS roles and nothing else.
If you have a print server with remote printing enabled, you can reduce the likelihood of an attack by applying principle of least privilege in the security settings. Follow Microsoft’s guideline:
To reduce the attack surface and as an alternative to disabling printing, check membership and nested group membership in the groups listed below. Attempt to reduce membership as much as possible, or completely empty the groups where possible. Due to legacy configurations and backwards compatibility, some of these groups may contain Authenticated Users or Domain Users, which would allow anyone in the domain to exploit the domain controller.
- Administrators
- Domain Controllers
- Read Only Domain Controllers
- Enterprise Read Only Domain Controllers
- Certificate Admins
- Schema Admins
- Enterprise Admins
- Group Policy Admins
- Power Users
- System Operators
- Print Operators
- Backup Operators
- RAS Servers
- Pre-Windows 2000 Compatible Access
- Network Configuration Operators Group Object
- Cryptographic Operators Group Object
- Local account and member of Administrators group