Sending Smartphones and Computers Out For Repair
When you send your smartphone out for repair, it is important to take steps to protect your personal and sensitive information. Here are some things you can do to help secure your smartphone when sending it out for repair:
-
Back up your data: Before you send your phone out for repair, make sure to back up your data. This way, you will have a copy of your important files and information in case something happens to your phone.
-
Factory reset your phone: A factory reset will erase all of the data on your phone, including your personal information, apps, and settings. This is a good way to make sure that your data is not accessible to anyone who works on your phone.
-
Remove your SIM card and any external storage: Your SIM card and any external storage (such as a microSD card) contain personal and sensitive information. Make sure to remove these before sending your phone out for repair.
-
Use a password or passcode: If your phone has a password or passcode, make sure it is enabled. This will help prevent unauthorized access to your phone while it is being repaired.
-
Consider using a service that offers secure shipping: Some repair services offer secure shipping options, such as shipping your phone in a locked box or using a courier service with secure tracking. This can help protect your phone while it is in transit.
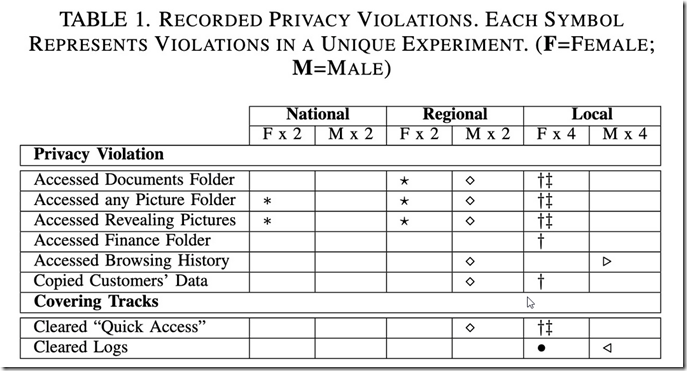
According to a university research study by Jason Ceci, Jonah Stegman and Hassan Khan, sending devices to repair shops carry inherent risk. The researches analyzed the device logs of 12 devices which they send to commercial repair shops. The logs showed the half of the technicians were involved in viewing data which were labeled ‘pictures’ and ‘finances’ and of those 2 were involved in copying the data to their own devices’.
According to the researchers:
Electronics repair and service providers offer a range of services to computing device owners across North America—from software installation to hardware repair. De-vice owners obtain these services and leave their device along with their access credentials at the mercy of technicians, which leads to privacy concerns for owners’ personal data. We conduct a comprehensive four-part study to measure the state of privacy in the electronics repair industry. First, through a field study with 18 service providers, we uncover that most service providers do not have any privacy policy or controls to safeguard device owners’ personal data from snooping by technicians. Second, we drop rigged devices for repair at 16 service providers and collect data on widespread privacy violations by technicians, including snooping on personal data, copying data off the device, and removing tracks of snooping activities.
To study the privacy policies and protocols, we visited eleven service providers—three national, three regional, and five local service providers. We also report our findings for two national smartphone repair service providers and for five device manufacturers.
• Privacy policies and the practice of communicating protocols and controls to protect customers’ data do not exist across service providers of all sizes.
• Service providers largely (10/11) require “all access” to the device, even when it is unnecessary.
• Technicians often snoop on customers’ data (6/16) and sometimes copy those to external devices (2/16).
• Technicians who violate privacy often do so carefully to not generate evidence (1/6) or remove such evidence (3/6).
• A significant proportion of broken devices (26/79, 33 percent) are not repaired due to privacy concerns. For the devices that get repaired, device owners are concerned about threats to their privacy but do not use the proper controls to protect their data.
In addition to these points, they also discovered that many broken devices do not get repaired out of privacy concerns. Here’s how you can get your device repaired and protect yourself from prying eyes:
- Encrypt or remove sensitive data before discarding devices or sending them out to repair.
- Don’t provide repair techs with your device’s password, it’s not required to perform hardware repairs.
- Data on laptops and computers can easily be accessed even without your password. Remove or encrypt the hard drive or delete all private data before sending it for repair.
- Choose a trusted device repair service center that has a written privacy policy.
For more details about the study, visit the publication site.
Discarding Electronics Safely
When you discard electronics, it is important to take steps to protect your personal and sensitive information. According to Comparitech.com, many devices being sold second hand are replete with personal data that can be easily accessed. The site purchased 200 hard drives that were sold second-hand from on-line marketplaces and analyzed them. According to their research:
- 26% were properly wiped and no remnant data could be recovered
- 26% had been formatted, but data could still be recovered with minimal effort
- 17% contained deleted data that could easily be recovered
- 16% of the hard disks appeared to have no attempt made to remove the data
- 16% were not accessible and could not be read
Their conclusion: “The problem is not that disks aren’t being wiped before resale, but that they aren’t being wiped properly.”
They also noted that photos and documents made up the bulk of the data recovered, however there were some notable exceptions:
- Photos of soldiers in the Middle East
- Passport scans
- Driver’s license scans
- Bank statements and utility bills
- Intimate photos
- A spreadsheet with the names and personal details of 113 people
- Completed tax documents (P60, W-9)
It’s important to note that business computers can contained cached copies of sensitive documents even if data is not kept on the local hard drive but rather on a network share. Even in cases where organizations have policies that require all data to be stored on shared folders, many employees maintain documents on their desktop and in their ‘my documents’ folders. For this reason, improper disposal of business computers pose a data privacy and security risk.
Here are some things you can do to help secure your electronics when discarding them:
-
Back up your data: Before you discard your electronics, make sure to back up your data. This way, you will have a copy of your important files and information in case something happens to your device.
-
Factory reset your device: A factory reset will erase all of the data on your device, including your personal information, apps, and settings. This is a good way to make sure that your data is not accessible to anyone who uses your device after you discard it.
-
Remove your SIM card and any external storage: Your SIM card and any external storage (such as a microSD card) contain personal and sensitive information. Make sure to remove these before discarding your device.
-
Use a secure method to destroy your data: If you are concerned about the possibility of someone being able to access your data even after you factory reset your device, you may want to use a secure method to destroy your data. This can include physically destroying the hard drive or using a program to overwrite the data with random characters.
-
Consider using a recycling service that offers secure data destruction: Some electronics recycling services offer secure data destruction as part of their process. This can help ensure that your personal and sensitive information is properly protected when you discard your electronics.