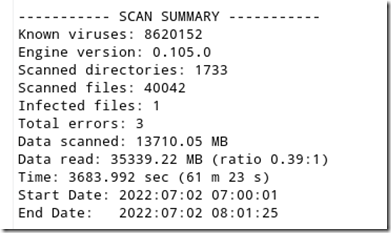
After years of running ClamAV scan on a Linux desktop without incident, I recently turned my gaze to the finished scan only to discover that the infected file count was not the usual zero. The scan summary revealed that a virus has been found!
I was so shocked that I almost choked on my pepperoni Hot Pocket.
I was in uncharted territory since this was the first time that Clam AV had detected an infection. Unlike commercially available AV products, the scan summary had no mention of the file name, location or type of malware that was found. As a security professional, it’s imperative to me to determine the type of malware that infects a system in order to take effective countermeasures. For example, finding a crypto-mining malware on a system in not a big deal, you can simply quarantine or delete it. Conversely, finding a keystroke logger means digging deeper into your system, determining the date it was installed and changing the passwords of any systems or services you logged on to since the time of infection.
Since ClamAV does not display the type of virus, location and other important pieces of information, here’s what you can do to get it:
Clamscan saves a log files to a hidden folder on your PC’s home directory, but only if you used the gui based scanner. The command line scanner will NOT save a log file be default. If you are using the command line scanner, append –l in order to create a log file. For example, the following command will scan your entire volume using recursion and deposit the log in in the default location.
sudo clamscan / –r –l
To be sure a log file is created, run clamscan using the –l (logging) option as shown above (you can also specify a log file name and location). The log file will by default be saved in the home directory in a hidden folder named clamtk.
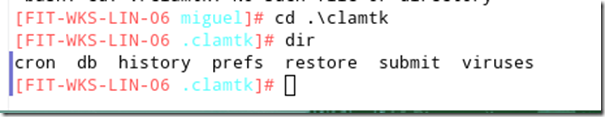
From your home directory, use the command cd .\clamtk to access the hidden clamtk directory as shown below.
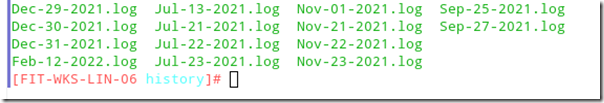
From there, change to the history directory and use ls or dir to view the historical log files.
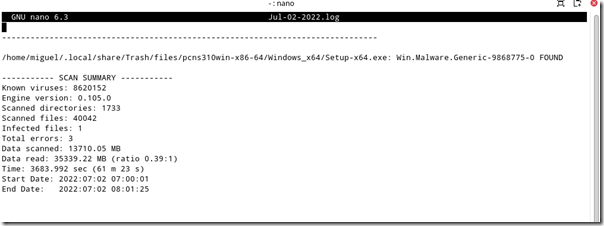
Use Vim, Nano or your favorite text editor to view the log file. The text log file will provide details including the infected file name, location and the type of malware.
In my case, the file came from a manufacturer’s Web site download years ago and had been sitting in my /trash folder. Given that this was the first time it was detected, it’s likely that it’s either a false positive or that new security researcher’s information has been made available about APIs used in the program’s code that may have it recently flagged as malware whereas it was not before.
To be on the safe site, I submitted the file to Virus Total and it came back clean, so apparently it was a false-positive. Seeing there was no more action to be taken, I re-ran clamscan with the –remove option in order to remove the file and got back to enjoying my lunch.

Matt
Miguel