Phishing emails often arrive disguised as internal users, however they are really from external email addresses. Many BEC (Business Email Compromise) and phishing attacks use obfuscation techniques to hide their true origin. BEC often involves domains that have similar-sounding wording in order to fool the recipient. In more careless instances, they arrive from Gmail or other public mail accounts.
We have all at some point received emails from our fake, doppelganger CEO, CFO or boss asking us to wire money, buy gift cards or perform a questionable task. After careful examination (such as clicking on the reply button) we realize that the true sender is from a totally different domain. For inexperienced users, it may be hard to discern well-crafter phishing emails from real ones.
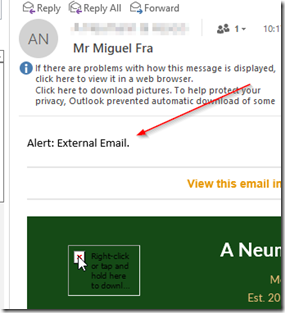
While many users are aware of these tricks, IT managers still lose sleep over the more careless users. So, what can be done to help prevent phishing and BEC attacks from similar sounding domain names? Providing a warning message that the email is from an external source is a good start. Here’s how to do it in Exchange server. The process is almost identical in Exchange 2013, 2016 and 2019 although the UI may look slightly different.
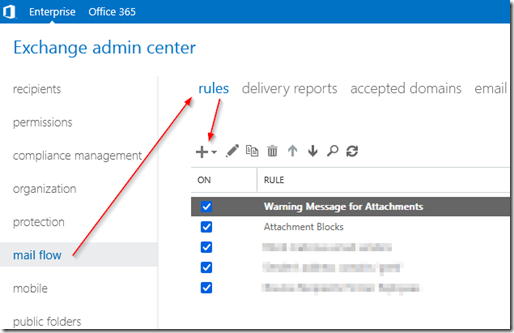
Open Exchange management console and go to mail flow –> rules. Click on the plus sign to create a new rule.
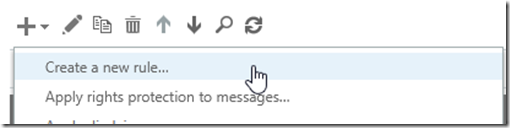
Click on create new rule.
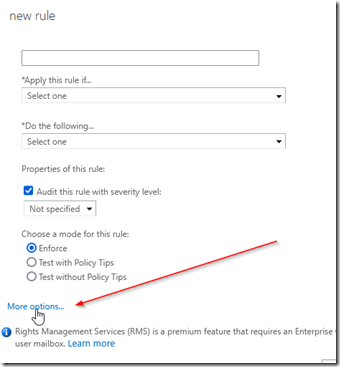
Click on more options to add optional menu choices.
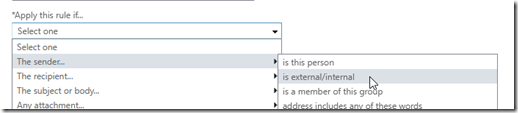
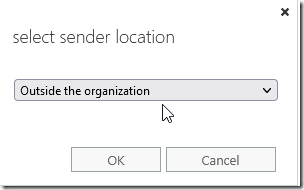
Give your rule a name the select apply this rule if… the sender –> is external/internal.
Choose outside the organization.
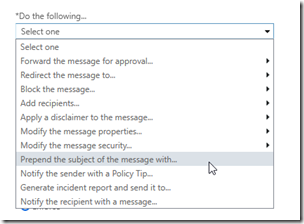
Now select: Do the following… Prepend the message with…
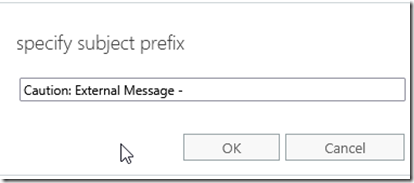
Add a warning message.
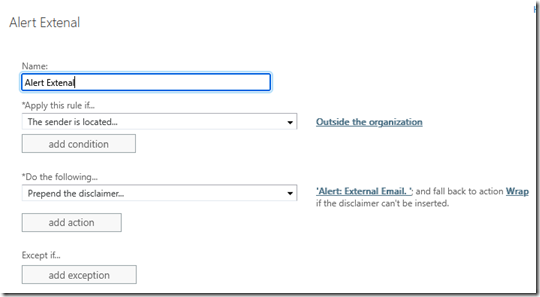
Your text and choices may vary but when finished, your rule should look similar to this:
Save the rule to finish. When a user receives a message from outside the domain, the warning message will appear at the beginning of the message as shown below.