The term PDC or Primary Domain Controller is a bit of a misnomer because ADDS DCs are set up in a way that their tasks are shared and objects can be added/modified by any DC in the ADDS forest (except those that are read-only). There are some specialized roles that are assigned to particular servers, these roles known as FSMO roles can be moved in a graceful fashion or seized by another DC if the DC which holds the role is no longer functioning.
FSMO stands for Flexible Single Master Operation. Active directory database follows multiple master model which means changes in active directory database get replicated to all the Domain Controllers in the domain. These roles are called Flexible Single Master Operation.
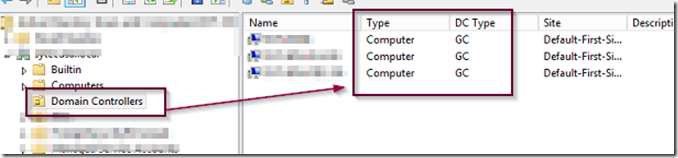
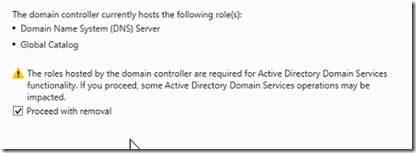
When you demote a domain controller, you need to make sure that you have another (or several other) functioning domain controllers in the forest so that the DC can transfer any FSMO roles it holds to another server. Before proceeding with a DC removal make sure you have at least one more domain controller with Global Catalog (GC) and DNS roles in the forest.
If you use this DC as a primary DNS resolver for the domain, you will need to start using another DNS server. After removing a DC, it’s not unusual to stumble across statically set DNS address on PCs, servers and other devices throughout the network. For this reason, I suggest setting aside the local IP address of the server you are going to demote and adding it to another DC/DNS server’s NIC card. This way, one of the other DNS servers can still resolve when queried using the removed DC’s IP address.
Open ADUC, expand domain controllers and make sure that there is at least one more DC with GC (Global Catalog) type available.
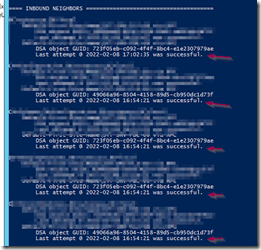
Run the command REPADMIN /SHOWREPL and check that all inbound and outbound partner DCs are replicating.
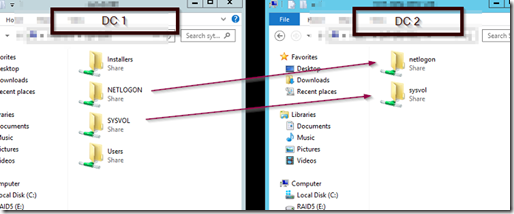
Use a UNC path and navigate to your DCs and verify that they have SYSVOL and NETLOGON shared.
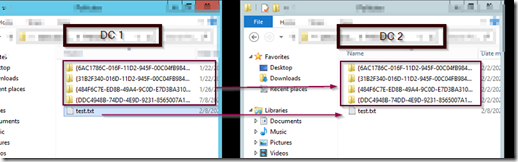
If you check the policies folder inside SYSVOL, you should see the same policy GUID across all DCs. Create a text file called test in the root of the policies folder and it should replicate to all other DCs in the forest.
Finally, check the DFSR event logs for any signs of replication errors and correct them if necessary. I know some of this may sound superfluous, but paranoia is not a bad thing when making changes to DCs. As with all changes, have a backup in case you need to revert due to some unforeseen circumstance. If you restore from backup, you can always perform a D2/D4 restore to get ADDS back to how it was.
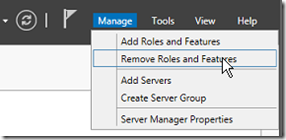
Open Server Manager and select remove roles and features.
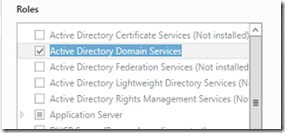
Uncheck the Active Directory Domain Services role.
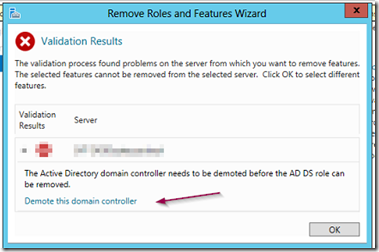
You will be presented with a dialog box that has a link for demoting ADDS.
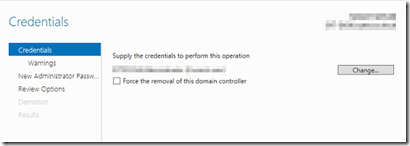
Select the link demote this domain controller. If you are logged in as a domain administrator, click next. Otherwise you will need to supply the credentials of a user with domain administrator privileges.
You will be warned about DNS and GC, click proceed.
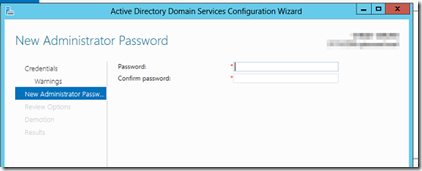
Enter a password which you will use to log in as a local administrator after the DC has been demoted and removed from the domain.
Finally, click on the demote button.
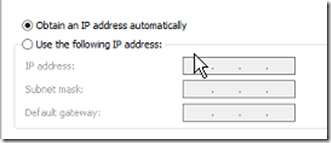
Once the DC has been demoted it will restart. After it boots up, set it’s IP address to dynamic.
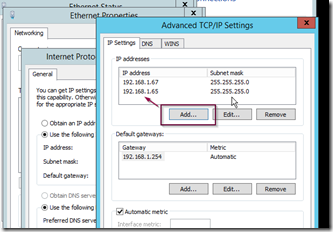
On another DC with DNS role installed, open its NIC properties and add the recently demoted DC’s IP address in the advanced TCP/IP settings as shown below.
This will allow any devices with statically set DNS address to resolve until you can purge all the old static DNS settings from the network devices.