A syslog server collects and stores firewall logs. Most halfway decent firewalls are able to output to a syslog server. Having a syslog server allows you to collect, store and analyze firewall logs and have greater control of your network. It can also help you detect internal malware, external attacks and Web surfing patterns.
Usually, syslog servers are found within the inside of the LAN. The one I will be setting up in this example however, is going to be focused on collecting data from remote servers. I manage several networks. Not all of them have their own syslog server. By having a Syslog server that collects remote data, I can point any our our client’s firewalls to send to our Syslog server whenever the need arises.
To begin, we are going to download and install Sourceforge’s Syslog Server, which happens to be free.
There isn’t much to the installation: next, next, next and finish!
Once installation is complete, open UDP port 514 on your firewall and port forward it to the Syslog Server’s local IP address.
Once the NAT rule for port 514 is in place, the Syslog Server is ready to receive data from a remote firewall.
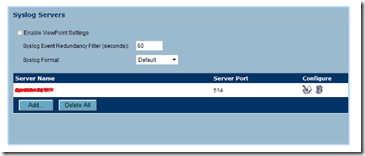
Log in to the remote firewall that you wish to capture data from and specify your Syslog Server’s FQDN or public IP address.
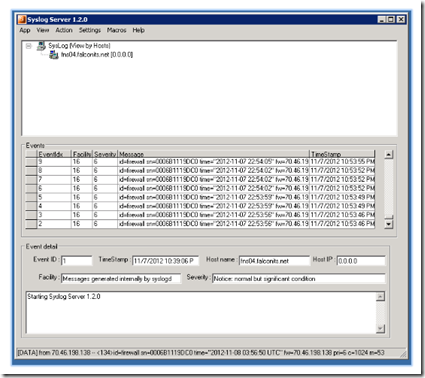
Your Syslog Server should begin receiving and logging the firewall’s packet data immediately.
Generally, I enable and disable the port 514 rule on the local firewall on an as-needed basis since I don’t use the Syslog data collection features all the time.