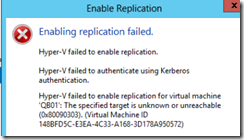
Hyper-V failed to enable replication and Hyper-V failed to authenticate using Kerberos authentication.
If you are using a slow VPN link, it’s possible that Kerberos is having trouble communicating over the VPN. Kerberos uses UDP by default which means that packets that arrive out of sequence are not reassembled. It’s a good idea to change Kerberos to use TCP when using it for authentication over a slow VPN link.
Instructions for both fixes are detailed below.
Configuring the Hyper-V Server’s Service Principal Name Attributes
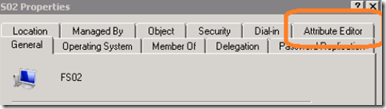
Open Active Directory Users and Computers (ADUC) and locate the virtual server host.
Right click on the server and select properties. In the properties windows, click on the attribute editor tab.
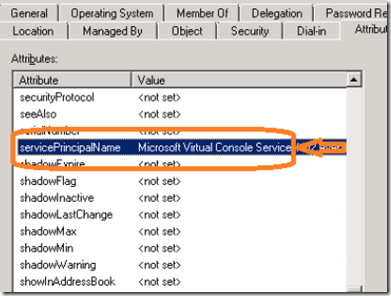
Highlight the ServicePrincipalName attribute and click on the edit button.
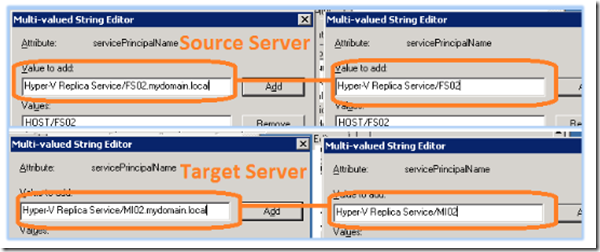
Add the following entries if they are not present or correct them if they are incorrect. You will need to do this step for both the source and the target server. Each attribute value must be entered with the corresponding server’s NetBIOS name as well as its FQDN.
For the source server:
Hyper-V Replica Service/SOURCESERVER
Hyper-V Replica Service/ SOURCESERVER.DOMAIN.LOCAL
Microsoft Virtual System Migration Service/ SOURCESERVER
Microsoft Virtual System Migration Service/ SOURCESERVER.DOMAIN.LOCAL
Microsoft Virtual Console Service/ SOURCESERVER
Microsoft Virtual Console Service/ SOURCESERVER.DOMAIN.LOCAL
For the target server (Server2):
Hyper-V Replica Service/ TARGETSERVER
Hyper-V Replica Service/ TARGETSERVER.DOMAIN.LOCAL
Microsoft Virtual System Migration Service/ TARGETSERVER
Microsoft Virtual System Migration Service/ TARGETSERVER.DOMAIN.LOCAL
Microsoft Virtual Console Service/ TARGETSERVER
Microsoft Virtual Console Service/ TARGETSERVER.DOMAIN.LOCAL
The example below illustrates the Hyper-V Replica Service SPN attribute ‘Hyper-V Replica Service’ entry for both the servers NetBIOS name as well as its FQDN on both the source and target servers.
Configuring Kerberos to Work over a Slow VPN Link
If you are using Hyper-V replica over a VPN tunnel, be aware that Kerberos authentication can be a bit tricky over a VPN tunnel. The reason is that Kerberos uses UDP by default, a connectionless protocol. Over a slow VPN or WAN link, the packets can arrive out of sequence. Unlike TCP, UDP will not reassemble the packets. Also, many VPN routers are configured to drop fragmented packets. This can also cause Kerberos authentication to fail.
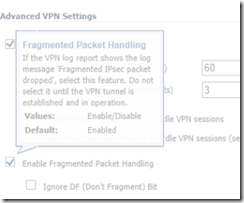
To fix this problem, make sure that your router is set to allow fragmented packets over the VPN tunnel and change Kerberos to use TCP rather than UDP as its default transmission protocol.
To enable fragmented packet handling, you will need to consult your VPN router’s installation guide. Each router will be different, depending on the brand and model.
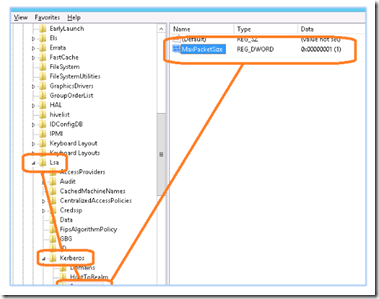
To force Kerberos to use TCP instead of UDP, open regedit and locate the following key:
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa\ Kerberos\Parameters
Create a DWORD MaxPacketSize
Change the value to 1 and restart your server. Note: You must make this registry change on both the source and target Hyper V servers and you must allow fragmented packet handling on both ends of the VPN tunnel.