Phishing can be more easily identified when the e-mail sender is coming from an unknown e-mail address or domain, but what about when the sender spoofs your real domain name?
Many users receive spoofed e-mail purportedly from business owners, managers and other contacts within their organization in an attempt to fool them into transferring money or divulging information. Spoofed emails also arrive from Microsoft, Ebay and other businesses, in attempts to get you to log in to fake Web site or install malicious ‘updates’.
Many organization use SPF (Sender Policy Framework) to declare which e-mail servers are the real servers that are authorized to send e-mail from their domains. When you enforce SPF, you can avoid the all-too-common spoofed e-mail trying to trick employees by masquerading as legitimate email.
In this exercise, we will use a registrar for DNS (Godaddy) to create an SPF record, then show you how to enforce SPF using ESET Protection for Exchange as well as in native Exchange server itself using anti-spam agents.
Creating a DNS SPF Record
To begin, we need to create an SPF record in your DNS zone for the e-mail domain. This will tell mail servers what IPs are authorized to send e-mail from your domain and help to prevent spammers from using your domain name to spoof others. Open the authorative zone in your DNS server and add a new record.
The record should look like this:
Type: TXT
Name: @
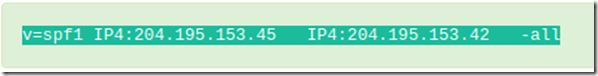
Value: v=spf1 IP4:204.195.153.45 -all
TTL: 12 hours (or anything you want really)
The type will be a TXT record and the name can be @ (for the root) or the host name of your mail server. The value will include: v=spf1 followed by the IP address of the mail server that is authorized to send for the domain. You can have multiple IP addresses if you have multiple e-mail servers, as shown below.
Finally, –all will indicate that all other IP addresses will be denied relay.
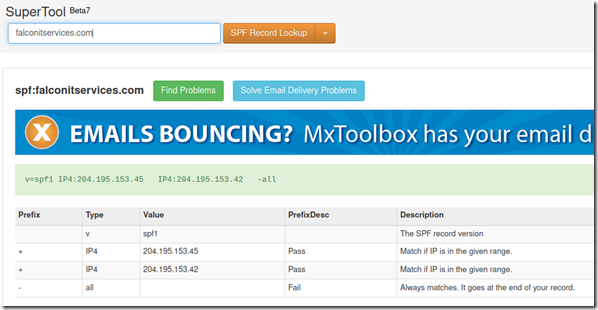
You can check MXToolbox shortly after you have created the SPF record; it should look similar to this:
Once you have completed the creation of a DNS SPF record, it will prevent your domain from being spoofed and fake emails containing your domain will not wind up in the mailboxes of organizations that enforce SPF rules.
Block Phishing/Spoofing with ESET Mail Protection
Next, we will use ESET to enforce SPF rules in Exchange server. To do this, log in to ESET ERA console and edit the policy for your Exchange server.
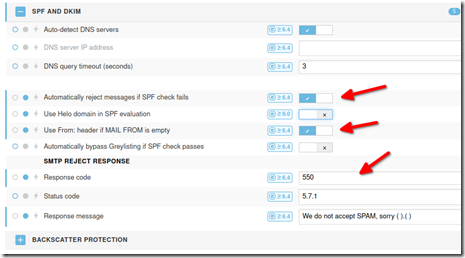
Under server –> antispam protection, enable message rejection on SPF fail, enable the use of from: header and write a lovely bounce message to our spammer friends.
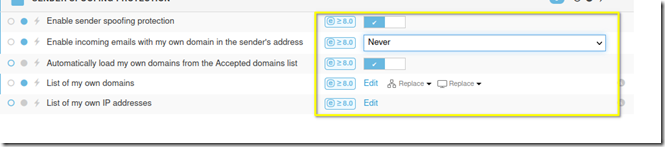
You can also create a rule is ESET under the sender proofing protection section to block spoofing. To do this, edit the following settings:
Enable the sender proofing protection and select ‘never’ allow emails that have your own domain unless they originate from the authorized IP list. Add your domain name to the domain list and your relay server’s IP address to the list of own addresses list.
Emails that contain your domain name in the sender’s field but do not originate from the authorized servers IP list will be rejected as SPAM.
Enforcing SPF with Exchange Anti-Spam Agents
If you don’t use ESET, you can still enforce SPF checks using the Microsoft Exchange Anti-Spam agents. You must install the Anti-Spam agents so that we can utilize the Sender ID agent to block non-authorized relay servers.
Enabling and Configuring Sender ID within Exchange 2013, 2016, 2019
After installing the antispam agents, the default configuration of the Sender ID for both SpoofedDomainAction and TempErrorAction is ‘Stampstatus’. This default action does not actually take any action against spoofed messages except to stamp the headers as likely SPAM. To block spoofed messages the SpoofedDomainAction should be set to Reject.
To set SpoofedDomainAction to Enabled run the following command in the Exchange Management Shell:
Set-SenderIDConfig -SpoofedDomainAction Reject
Restart the transport service for the changes to take effect and Exchange will block Emails that do not comply with SPF.