Aside from antivirus email scanning, it’s important to block dangerous file attachments from reaching users in your organization. The first reaction I get from managers when I request file blocking is that they need to have access to sending and receiving certain types of files, such as ZIP, RAR, etc. Blocking these files creates an added layer of security by requiring the sender and recipient to perform a manual security ‘handshake’. This handshake add security be having the sender and recipient discuss exchanging the file, eliminating the files send by email by spammers or infected PC’s. Of course, the sender and recipient would have to send the file by another means, such as a file exchange service like SeaFile.
How to Block Dangerous File Type in Office 365/ Exchange
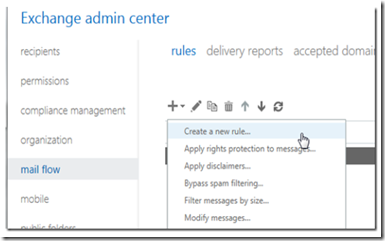
Open the Exchange admin panel and navigate to mail flo –> rules and click + to add a new rule.
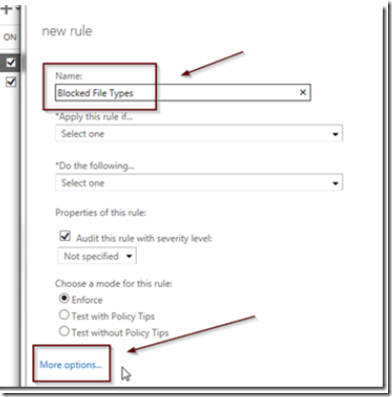
Give your rule a name and click on more options at the bottom of the windows to display more options.
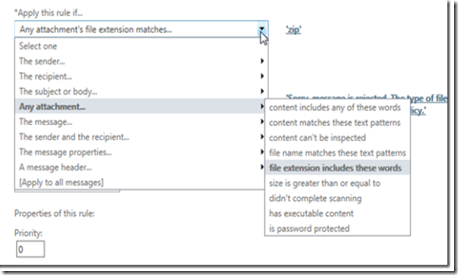
Create a rule that flags any attchments that have specific file name pattern.
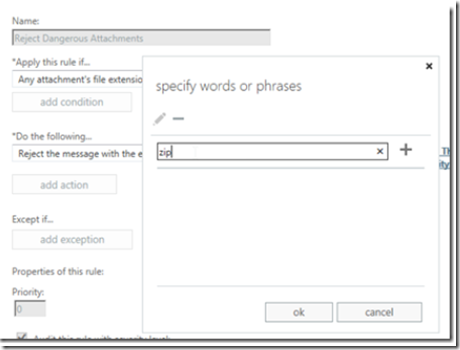
Then add the file name extensions that you wish to block, excluding the dot.
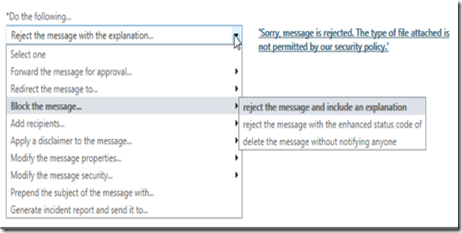
Now select a response (such as email rejection) and include a rejection message
Click the save button when finished.
You may go back and click on the hyperlinked attachment types to add or remove attachments if you need to do so in the future.
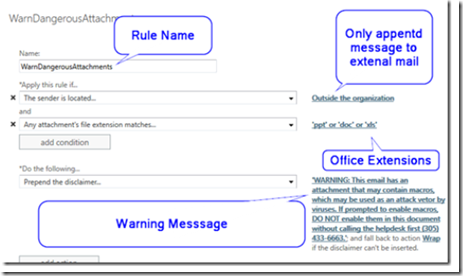
Creating a Warning Message Rule for Office Documents
Since MS office documents (DOC, XLS and PPT) can contain macros, it’s a good idea to send the user a warning message telling him/her to be careful and not allow Macros if requested, without consulting the sender or the helpdesk first. To do so, use the following setting after creating a new rule:
When someone outside the organizations sends an email to an internal mailbox, the message will be preceeded by a warning.
Here is a list of dangerous attachment types and their extensions for you to block:
.EXE – An executable program file. Most of the applications running on Windows are .exe files.
.PIF – A program information file for MS-DOS programs. While .PIF files aren’t supposed to contain executable code, Windows will treat .PIFs the same as .EXE files if they contain executable code.
.APPLICATION – An application installer deployed with Microsoft’s ClickOnce technology.
.GADGET – A gadget file for the Windows desktop gadget technology introduced in Windows Vista.
.MSI – A Microsoft installer file. These install other applications on your computer, although applications can also be installed by .exe files.
.MSP – A Windows installer patch file. Used to patch applications deployed with .MSI files.
.COM – The original type of program used by MS-DOS.
.SCR – A Windows screen saver. Windows screen savers can contain executable code.
.HTA – An HTML application. Unlike HTML applications run in browsers, .HTA files are run as trusted applications without sandboxing.
.CPL – A Control Panel file. All of the utilities found in the Windows Control Panel are .CPL files.
.MSC – A Microsoft Management Console file. Applications such as the group policy editor and disk management tool are .MSC files.
.JAR – .JAR files contain executable Java code. If you have the Java runtime installed, .JAR files will be run as programs.
.BAT – A batch file. Contains a list of commands that will be run on your computer if you open it. Originally used by MS-DOS.
.CMD – A batch file. Similar to .BAT, but this file extension was introduced in Windows NT.
.VB, .VBS – A VBScript file. Will execute its included VBScript code if you run it.
.VBE – An encrypted VBScript file. Similar to a VBScript file, but it’s not easy to tell what the file will actually do if you run it.
.JS – A JavaScript file. .JS files are normally used by webpages and are safe if run in Web browsers. However, Windows will run .JS files outside the browser with no sandboxing.
.JSE – An encrypted JavaScript file.
.WS, .WSF – A Windows Script file.
.WSC, .WSH – Windows Script Component and Windows Script Host control files. Used along with with Windows Script files.
.PS1, .PS1XML, .PS2, .PS2XML, .PSC1, .PSC2 – A Windows PowerShell script. Runs PowerShell commands in the order specified in the file.
.MSH, .MSH1, .MSH2, .MSHXML, .MSH1XML, .MSH2XML – A Monad script file. Monad was later renamed PowerShell.
.SCF – A Windows Explorer command file. Could pass potentially dangerous commands to Windows Explorer.
.LNK – A link to a program on your computer. A link file could potentially contain command-line attributes that do dangerous things, such as deleting files without asking.
.INF – A text file used by AutoRun. If run, this file could potentially launch dangerous applications it came with or pass dangerous options to programs included with Windows.
.REG – A Windows registry file. .REG files contain a list of registry entries that will be added or removed if you run them. A malicious .REG file could remove important information from your registry, replace it with junk data, or add malicious data.
.DOCM, .DOTM, .XLSM, .XLTM, .XLAM, .PPTM, .POTM, .PPAM, .PPSM, .SLDM – New file extensions introduced in Office 2007. The M at the end of the file extension indicates that the document contains Macros. For example, a .DOCX file contains no macros, while a .DOCM file can contain macros.
.GZ GNU Zipped Archive Files
.ACE Priprietary compression file archive compressed by WinAce
.ZIP & .RAR Compression files used to obfuscate malware.