The issue at hand is when ESET displays an PUA alert when a server restart and you have a server with Broadcom NIC adapters, not Intel.
Program name: C:\Windows\Temp\UID\miniunz.exe
User name: NT AUTHORITY\SYSTEM
Infected object: File file:///C:/Windows/TEMP/76274e03‑4a2a‑4342‑81df‑2afd7897f45f/NIC_Intel_Firmware/iqvw64e.sys D04E5DB5B6C848A29732BFD52029001F23C3DA75
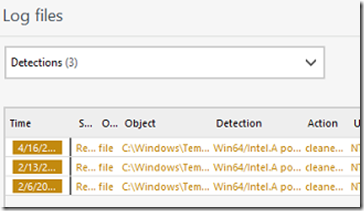
Virus name: 26906 (20230315) Potentially unsafe application Win64/Intel.A
I was able to recreate the issue by restarting the server. Each time, ESET logged a detection as shown below. Apparently an application was downloading an old driver (which has a vulnerability) to the temp folder. The drive itself is not malicious however it can be exploited and thus ESET flagging it as potentially unwanted.
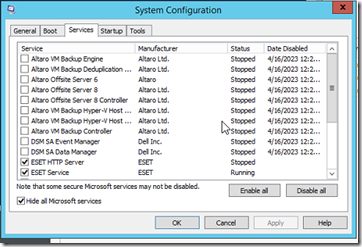
To discover the culprit, I proceeded to run MSCONFIG and restarted the server with only the Microsoft services and ESET enabled.
After a fresh restart, the issue did not reoccur. At this point I began to add startup services one at a time while restarting the server.
So who was the offending service? Dell OpenManage 8.2 it appears, since the issue ceased once the services ‘DSM SA*’ were stopped.
After an in-place upgrade to OMSA version 9.3 (the recommended version for that server model with 2012R2), the server rebooted without and the issue no longer presented itself.